August 13, 2018

Two recently discovered vulnerabilities in the fax protocol can transform fax machines into entry points for hackers into corporate networks, two Check Point researchers revealed last week in a talk given at the DEF CON 26 security conference held in Las Vegas.
Named “Faxploit,” this attack targets the ITU T.30 fax protocol, according to a copy of the DEF CON presentationgiven by Eyal Itkin and Yaniv Balmas last week.
More specifically, Faxploit leverages two buffer overflows in the fax protocol components that handle DHT and COM markers —CVE-2018-5924 and CVE-2018-5925, respectively.
Fax machines used as entry points into corporate networks
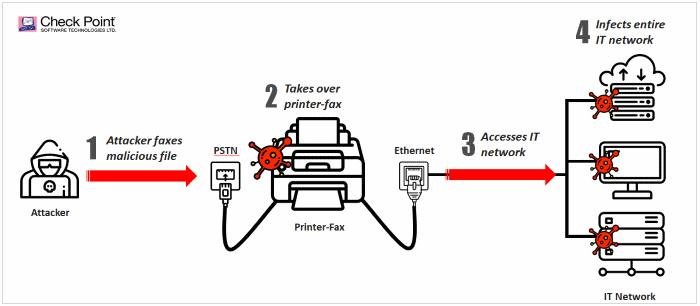
Itkin and Balmas say that an attacker can send malformed fax images to a fax machine containing code that exploits these two vulnerabilities and then gain remote code execution rights over the targeted device, allowing the hacker to run his own code and take over the machine.
From here, they say that an attacker can download and deploy other hacking tools that scan the local network and compromise nearby devices.
The two researchers have recorded a demo of a Faxploit attack that compromises a fax machine and then uses this machine to download and deploy the EternalBlue exploit that infects nearby computers exposed via the SMB protocol.
Faxploit carried out via phone lines, not Internet connection
Itkin and Balmas say the Faxploit attack is dead simple, as a hacker only needs the victim’s fax number to target an organization.
Furthermore, no direct Internet connection is needed to the actual fax machine as the attack code comes in via the phone line. This also makes preventing Faxploit almost impossible, as no security software scans incoming faxes.
The only way to prevent Faxploit attacks is to apply patches to individual fax machines and all-in-one office printers, which also come with an embedded fax machine.
HP released patches, other fax vendors vulnerable too
At the time of writing, only HP has addressed Faxploit. The company released patches last week for HP Officejet all-in-one printers, the fax machine that the Check Point researchers used for recording their demo video.
“We strongly believe that similar vulnerabilities apply to other fax vendors too as this research concerns the fax communication protocols in general,” Check Point said today.
But while other vendors test their devices and release patches in the coming months, there is also a way to limit the impact of Faxploit attacks, if they ever happen.
Itkin and Balmas say the simplest defense to neutralize Faxploit attacks is network segmentation. By breaking large corporate networks into smaller ones or by isolating fax machines on their own subnetworks, companies can limit the type of data an attacker can gain access to via this attack.

